Nowadays, e-mails are one of the main forms of online communication. Through them, you can share files, send messages, and keep in touch with friends, family, and colleagues. However, while e-mails are a useful tool, they are also vulnerable to errors and security problems. That is why it is important to know how to verify emails, to ensure that we are sending and receiving accurate and secure information.
In this article, we will discuss some ways to verify emails to make sure they are legitimate and secure. We will discuss how to verify the sender’s email address, how to check attachments, how to check if an email is a phishing email, and how to protect our own email address.
1. Verify the sender’s e-mail address
One of the first steps to take when verifying an email is to check the sender’s email address. Fraudulent e-mails often use domain names similar or even identical to those of legitimate companies, but with minor differences. For example, a fraudulent email that appears to be from “paypal.com” could actually be from “paypall.com” or “pay-pal.com”. It is important to carefully verify the sender’s email address before clicking on any links or downloading any attachments.
2. Review attachments
Attachments can be another source of email security problems. It is important to verify any attachment before downloading or opening it. Attachments may contain viruses, malware, or malicious links. If you are not expecting an attachment, it is best not to open it. If you are expecting an attachment, it is important to verify that it is from a legitimate source before opening it.
3. Checking if an email is a phishing email
Phishing emails are a common type of online fraud that impersonates a legitimate company or person to obtain personal or financial information. It is important to know how to recognize a phishing email to avoid falling into the trap. Some warning signs include:
- Requests for personal or financial information, such as passwords, credit card numbers, or bank account information.
- Suspicious links that do not appear to go to a company’s legitimate website or contain misspellings.
- Messages of urgency or threats of negative consequences if immediate action is not taken.
- Requests to transfer money or click on links that may appear suspicious.
If an email is suspected to be a phishing email, it is important not to provide personal or financial information and not to click on any links. Instead, the legitimate company or individual should be contacted by phone or email using the contact information on their official website.
4. Protecting our own e-mail address
Finally, it is important to protect our own e-mail address from being compromised or used for malicious purposes.
Professional email verification services use a combination of techniques to validate and verify the authenticity of email addresses. The following are some of the most common techniques used in these services:
1. Syntactic validation: This technique involves verifying whether the e-mail address complies with the formatting and syntax standards established by the industry. Syntactic validation is performed by using algorithms and patterns that check whether the e-mail address contains the appropriate characters and structures.
Domain validation: Domain validation involves verifying whether the domain of the e-mail address is valid and exists. This technique involves checking whether the domain’s mail server is active and able to receive emails.
3. Validation of the e-mail account: Email account validation involves verifying whether the email account exists and is valid. This technique is performed by sending a test email to the email address and checking for a valid response.
4. Disposable e-mail address validation: E-mail verification services may also use techniques to identify and remove disposable or temporary e-mail addresses, which are created for temporary use and deleted after a specified period of time.
5. Bulk email verification: Email verification services also offer bulk verification options that allow users to verify large numbers of email addresses at the same time.
6. Third-party email verification: Some email verification services also use third-party databases and email verification tools to check the authenticity of email addresses.
In summary, professional email verification services use a combination of syntactic validation techniques, domain validation, email account validation, disposable email address verification and third-party email verification tools to validate and verify the authenticity of email addresses.
how we can use an api to validate an email
To use an API to verify an e-mail, the following steps must be followed:
Register for an API key: Before you can use an email verification API, you need to register and obtain an API key. Most service providers offer different pricing plans to suit the user’s needs.
2. Integrate the API into your application or website: Once the API key has been obtained, it must be integrated into your application or website. This involves the implementation of the programming logic required to make API calls and receive the corresponding responses.
3. Send verification request: Once the API is integrated into your application, you can send verification requests to the API. The request will include the e-mail address to be verified.
4. Receive API response: After submitting the verification request, the API will process the request and send a response. The response will include information about whether or not the e-mail address is valid, and may also include additional information about the e-mail address, such as the domain name and other details.
5. Take action based on the response: After receiving the API response, it is important to take appropriate action based on the information received. For example, if the e-mail address is invalid, you may want to ask the user to provide a valid e-mail address. If the e-mail address is valid, you can continue with the registration process or send e-mails.
In summary, to use an email verification API, you need to register for an API key, integrate the API into your application or website, send verification requests, receive responses from the API, and take action based on the response received.
I will give you an example of how we have implemented the API to verify emails in Google Sheets to verify emails. The same that applies to Google Sheets can be used in Google Forms or in tools such as Excel. The principle is the same.
To verify an email in Google Sheets we must create a script that makes the API calls. As you can see in the image the invocation is very simple, we only have to make the Rest call.
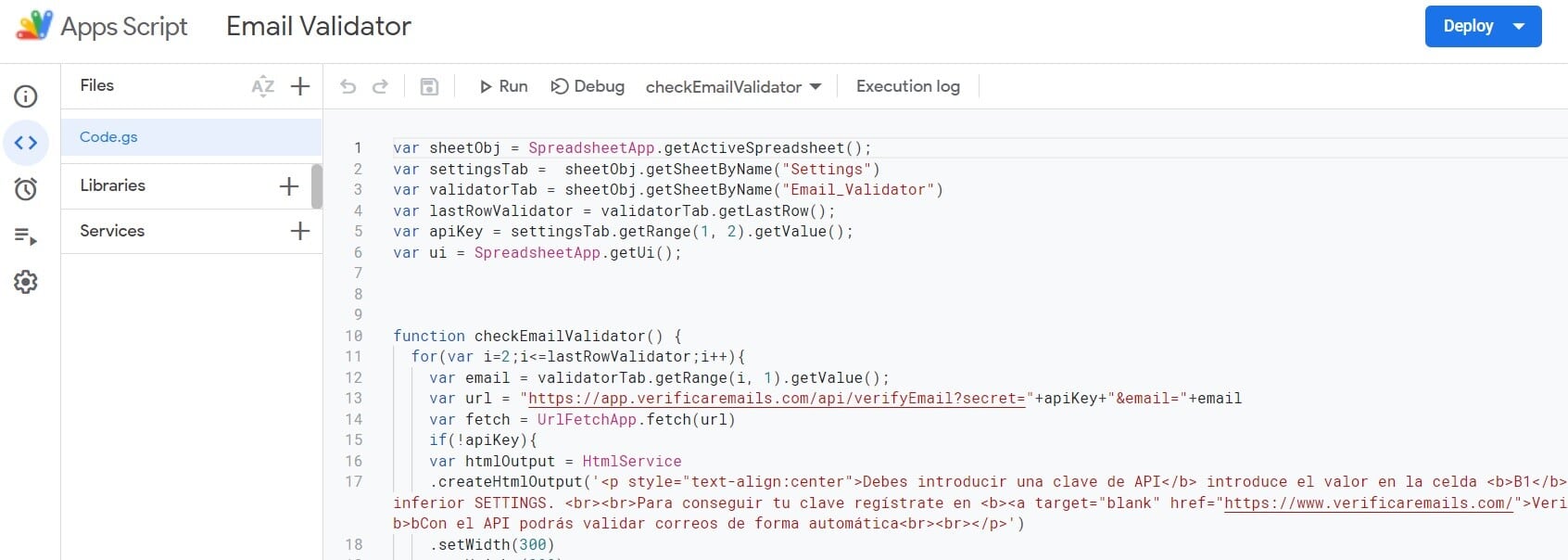
In the case of the implementation we have carried out, the mail validation process is launched by clicking on a menu option that calls the Google Sheets App Script function. This is fully customizable.
If you are a Verificaremails customer and you want to have access to the email verification sheet with Google Sheets, please contact us through the form and we will give you access.
To finish and not to extend more you have seen how to verify emails using an implementation of the API. The main techniques used by professional verification services and how we can manually validate the veracity of an email address that sends us a message. I hope you liked it 😉